Understanding Cross-Account Access in AWS
In modern cloud environments, managing access across multiple AWS accounts is a common challenge. Whether you’re operating within a multi-account AWS organization or collaborating with external partners, AWS provides robust mechanisms for secure cross-account access. This blog post will break down how cross-account access works and the best practices for implementing it.
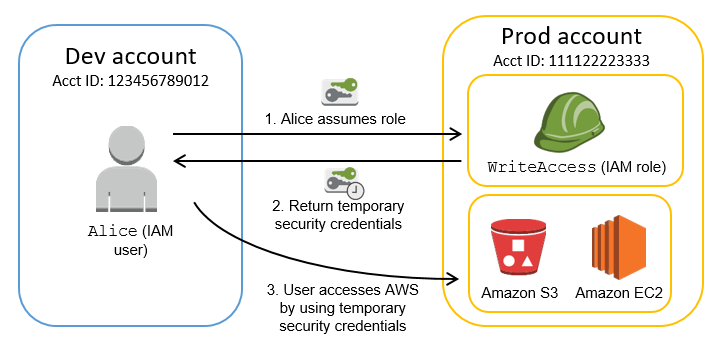
What is Cross-Account Access in AWS?
Cross-account access in AWS allows users, roles, or services in one AWS account to access resources in another account. This eliminates the need to share long-term credentials while maintaining security and control over permissions.
Methods for Implementing Cross-Account Access
AWS provides multiple ways to enable secure access between accounts. The most commonly used methods include:
1. Resource-Based Policies
Resource-based policies are attached directly to AWS resources, specifying which external AWS accounts or principals (users, roles) can access them.
Use Case:
- Ideal when you want to grant access to specific resources without modifying the principal’s permissions.
Example:
- An Amazon S3 bucket policy that grants another AWS account permission to read from the bucket.
2. IAM Roles with Trust Relationships
IAM roles are a powerful way to delegate permissions across AWS accounts securely. A trust relationship specifies which external AWS accounts can assume the role.
Use Case:
- Suitable when the resource does not support resource-based policies or when centralizing permission management is preferred.
Example:
- An IAM role in Account A allows a user from Account B to assume the role and access resources in Account A.
Steps to Implement Cross-Account Access Using IAM Roles
To configure secure access using IAM roles, follow these steps:
Step 1: Create a Role in the Resource Account
- Define an IAM role in the AWS account where the resource is located.
- Attach a permissions policy that specifies allowed actions on the resource.
Step 2: Configure the Trust Relationship
- Set up a trust policy that defines which AWS accounts (or specific IAM users/roles) are allowed to assume the role.
Step 3: Assume the Role from the External Account
- The external AWS account can assume the role using AWS Security Token Service (STS).
- The AWS user or service in the external account receives temporary credentials to access the specified resources.
Real-World Example: Sharing S3 Access Across Accounts
Consider an organization with two AWS accounts:
- Account A (Production Environment)
- Account B (Development Environment)
Developers in Account B need to access an S3 bucket in Account A.
Solution:
- In Account A:
- Create an IAM role granting the necessary S3 permissions.
- Set a trust policy allowing the role to be assumed by users from Account B.
- In Account B:
- Developers assume the IAM role from Account A using STS.
- Temporary credentials are used to access the S3 bucket securely.
Best Practices for Cross-Account Access
To ensure security and compliance, follow these best practices:
- Use IAM roles instead of IAM users to avoid long-term credentials.
- Implement least privilege access by granting only necessary permissions.
- Monitor access logs using AWS CloudTrail for auditing and compliance.
- Regularly review permissions to remove unnecessary access.
Conclusion
Cross-account access in AWS provides a secure and efficient way to manage permissions across multiple AWS accounts. By leveraging resource-based policies and IAM roles with trust relationships, organizations can ensure secure collaboration without compromising security.
For a detailed walkthrough, refer to the AWS IAM documentation on delegating access across AWS accounts.