AWS Key Management Service (KMS)
1. Introduction
When one speaks of encryption in AWS, it is essential to immediately consider AWS KMS. The service abstracts much of the complexity involved in managing cryptographic keys while providing robust integration with other AWS services such as Amazon S3, Amazon EBS, Amazon RDS, Amazon Redshift, and AWS Systems Manager, among others. Whether accessed through the AWS Management Console, Command Line Interface (CLI), or Software Development Kits (SDKs), AWS KMS provides a consistent interface for interacting with encryption keys.
AWS KMS simplifies the process of encryption by integrating with AWS Identity and Access Management (IAM) for authorization, ensuring that only users or roles with proper permissions can perform cryptographic operations. The service also offers extensive audit capabilities via AWS CloudTrail, enabling organizations to track every use of their keys for compliance and security purposes.
In this chapter, we will delve into the specifics of AWS KMS, exploring its various components and explaining how they interact to provide a secure, scalable key management solution. We will cover everything from the basic concepts of symmetric and asymmetric keys to advanced topics such as envelope encryption and attribute‐based access control (ABAC).
2. Core Concepts
AWS KMS is built on several core concepts that form the foundation for secure key management. Understanding these concepts is essential for both designing secure systems and for preparing for professional certification exams.
2.1. Symmetric vs. Asymmetric Keys
At the heart of cryptographic systems lie two fundamental types of encryption keys: symmetric keys and asymmetric keys.
Symmetric Keys
Symmetric encryption involves a single cryptographic key that is used for both encryption and decryption. This approach is inherently fast and efficient, making it ideal for encrypting data where performance is a primary concern. In AWS KMS, symmetric keys were the original offering and remain the most commonly used key type for many integrated services.
Key characteristics of symmetric keys in AWS KMS include:
- Single Key Usage: A single key encrypts and decrypts data.
- Envelope Encryption: Many AWS services leverage symmetric keys to implement envelope encryption, whereby a data key is generated, used for client-side encryption, and then encrypted with a master key.
- API-Only Access: The unencrypted key material never leaves KMS; all cryptographic operations are performed via API calls. This means users or applications never directly access the raw key.
- Performance Efficiency: Because symmetric key algorithms are generally faster, they are well-suited for handling bulk data encryption.
Asymmetric Keys
In contrast, asymmetric encryption uses a pair of keys—a public key and a private key. The public key can be shared openly, while the private key is kept secret. This key pair mechanism facilitates encryption and decryption where the roles of the keys are distinct.
Key characteristics of asymmetric keys in AWS KMS include:
- Key Pair Structure: A public key encrypts data or verifies a signature, while the private key decrypts data or creates a signature.
- External Use Cases: Asymmetric keys are especially useful in scenarios where data must be encrypted outside of AWS or when communicating securely with external parties.
- Downloadable Public Key: AWS KMS permits the download of the public key so that external applications can encrypt data before sending it to KMS for decryption.
- Limited Direct Access: Even with asymmetric keys, the private key is never available in an unencrypted form. All operations that involve the private key must be performed via the KMS API.
The choice between symmetric and asymmetric keys depends on the use case. Symmetric keys are preferred when high performance and simplicity are required, whereas asymmetric keys are used when secure key exchange or digital signature operations are necessary.
2.2. Key Management Types
AWS KMS supports several types of keys, each with distinct management characteristics and use cases. These key types determine not only how keys are created and managed but also who is responsible for their lifecycle and rotation.
2.2.1. Customer-Managed Keys
Customer-managed keys (CMKs) are created, managed, and used by the customer. These keys provide a high degree of control and flexibility:
- Creation and Management: Customers can create CMKs directly in AWS KMS and manage them throughout their lifecycle.
- Rotation Policies: CMKs can be configured for automatic rotation—typically every year—or rotated on-demand. When rotation is enabled, the old key remains available for decryption while a new backing key is used for subsequent operations.
- Key Policies and Auditability: Customers can define custom key policies to specify which users and roles have access to the key. Every operation using these keys is auditable via CloudTrail, offering full visibility over their usage.
- Use in Envelope Encryption: CMKs are commonly used as the master keys in envelope encryption, where a data encryption key (DEK) is generated and then wrapped by the CMK.
Because CMKs are fully under the customer's control, they are ideal for applications requiring stringent security controls and full traceability of key usage.
2.2.2. AWS-Managed Keys
AWS-managed keys are created, managed, and rotated automatically by AWS. These keys are used exclusively by AWS services:
- Service-Specific Keys: When you use an AWS service (such as Amazon S3 or Amazon EBS) that integrates with KMS, the service typically uses an AWS-managed key.
- Automatic Rotation: AWS-managed keys are rotated automatically every year, eliminating the need for customer intervention.
- Limited Customization: Although you can view the key metadata and audit its usage, you do not have the ability to modify key policies or change the rotation schedule.
- Operational Simplicity: AWS-managed keys provide a “set-and-forget” solution, ensuring that encryption is handled transparently without requiring in-depth key management knowledge.
These keys are best suited for customers who want robust encryption without the overhead of managing keys manually.
2.2.3. AWS-Owned Keys
AWS-owned keys are created, managed, and used exclusively by AWS on behalf of multiple customers:
- Internal Use Only: These keys are used by AWS services to protect resources but are not visible or accessible within the customer’s AWS account.
- No Direct Control: Customers cannot view, manage, track, or audit AWS-owned keys. AWS provides assurances regarding their existence and security but leaves all operational aspects under AWS’s purview.
- Cross-Account Utility: Although AWS-owned keys might protect resources that span multiple accounts, customers have no direct interaction with these keys.
- Operational Transparency: These keys are fully abstracted away from the customer’s management interface, simplifying operations for scenarios where individual key management is not necessary.
AWS-owned keys are typically used in scenarios where AWS manages the full lifecycle of the key to secure services without customer intervention.
3. Key Creation and Material Origin
When creating a KMS key, one of the first decisions is how the key material—the raw bits that constitute the cryptographic key—is generated and managed. This decision is permanent for a given key and impacts security, compliance, and operational control.
3.1. KMS-Generated Keys
In the default mode of operation, AWS KMS generates the key material internally:
- Automated Generation: AWS automatically creates, stores, and manages the cryptographic key material within its secure key store.
- High Security: Because the key material is generated within a hardened, audited environment, customers can be assured that the key material is not exposed externally.
- Simplified Management: With KMS-generated keys, there is no need for customers to manage external key material. The entire lifecycle, from generation through rotation and deletion, is handled by AWS.
- Encryption Integration: These keys are designed to work seamlessly with envelope encryption patterns, where the generated key serves as the master key to wrap data keys generated via the GenerateDataKey API.
This model is ideal for most applications where the customer trusts AWS’s security controls and prefers to offload the complexity of key generation and secure storage.
3.2. External Key Material
In certain scenarios, customers may require that key material be generated outside of AWS KMS. This model, known as “Bring Your Own Key” (BYOK), provides additional control:
- Manual Import: Customers generate the key material externally, using their own cryptographic systems, and then import it into AWS KMS.
- Control and Compliance: Organizations that have strict regulatory or compliance requirements might prefer to generate key material in a controlled environment before bringing it into AWS.
- Limited Rotation: When using externally generated key material, customers are responsible for its lifecycle management. Automatic rotation is not available, so keys must be rotated on-demand.
- Use Cases: This approach is often used when an organization already has a robust cryptographic infrastructure or when the security policy requires that keys are generated in a specific hardware security module (HSM) environment before import.
Using external key material allows organizations to integrate AWS KMS into existing security architectures while maintaining control over the cryptographic roots of trust.
3.3. Custom Key Stores with AWS CloudHSM
For customers who require direct control over the hardware that stores their key material, AWS offers the option of using a custom key store backed by AWS CloudHSM:
- Dedicated Hardware Security: AWS CloudHSM provides dedicated hardware security modules that customers control. By linking a CloudHSM cluster to KMS, customers ensure that key material is generated and stored on hardware they manage.
- Custom Key Store Configuration: Customers first set up a CloudHSM cluster across multiple Availability Zones for high availability. This cluster is then connected to AWS KMS via a custom key store configuration.
- Operational Integration: Although the key material is stored within the customer-controlled HSM, AWS KMS continues to manage key metadata, enforce policies, and log cryptographic operations.
- Enhanced Security and Compliance: This option is particularly valuable for highly regulated industries or for organizations with strict internal security requirements, as it provides tangible control over the hardware used for key storage.
- Performance Considerations: Cryptographic operations that involve keys stored in a custom key store may have different performance characteristics than those using KMS-generated keys; however, the benefits in terms of security and compliance often outweigh these considerations.
By choosing a custom key store with AWS CloudHSM, customers can align their cryptographic operations with stringent regulatory requirements while still benefiting from the operational simplicity of AWS KMS.
4. Multi-Region Keys
As organizations increasingly operate in global, multi-region environments, the need for keys that can be replicated across regions becomes critical. AWS KMS provides the ability to create multi-region keys, which simplify cross-region encryption and decryption workflows.
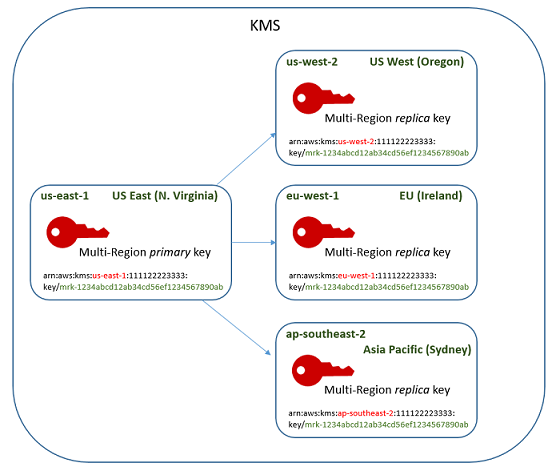
Multi-region keys are designed for scenarios where data may be encrypted in one region and decrypted in another, without the need for re-encrypting data or incurring cross-region API calls:
- Replication of Key Material: When a multi-region key is created, its key material and key ID are replicated across multiple AWS Regions. Despite residing in different regions, the key retains the same key ID and properties.
- Primary and Replica Model: Multi-region keys follow a primary/replica model. One region hosts the primary key, and additional regions host replica keys. Although each key can be managed independently, they are functionally equivalent and share the same underlying cryptographic material.
- Disaster Recovery and Global Applications: Multi-region keys are particularly useful for disaster recovery scenarios, where an application’s data is stored in one region but must be accessible in another. They also support global client-side encryption workflows, enabling low-latency decryption in multiple regions.
- Automatic Rotation: When automatic rotation is enabled on the primary key, the updated backing key is replicated to all replica keys, ensuring consistent key management across regions.
- Operational Considerations: Although multi-region keys provide the convenience of cross-region encryption and decryption, it is important to note that they are not “global” keys. Instead, each key is bound to a specific region; therefore, proper planning and management are required when designing multi-region architectures.
By leveraging multi-region keys, organizations can streamline data protection in globally distributed applications, reduce latency, and simplify key management in disaster recovery scenarios.
5. Envelope Encryption
Given that AWS KMS imposes a limit on the size of data that can be directly encrypted (up to 4 kilobytes), AWS recommends using envelope encryption for larger data sets. Envelope encryption is a hybrid approach that leverages both AWS KMS and client-side encryption.
5.1. GenerateDataKey API
The GenerateDataKey API is central to the envelope encryption process:
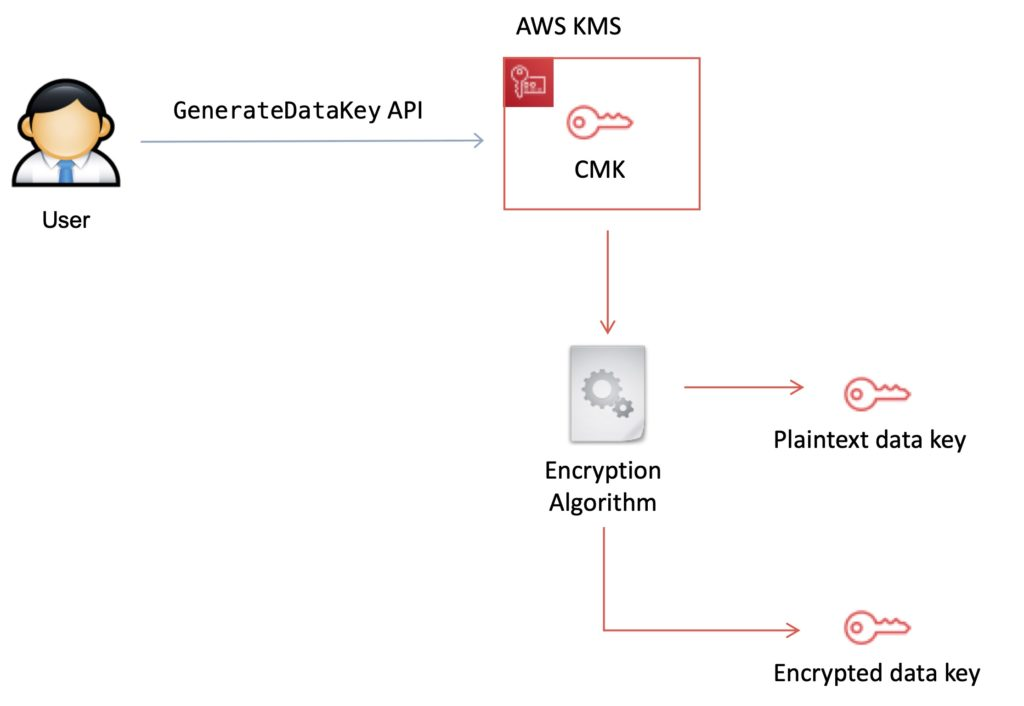
- Two-Part Output: When the GenerateDataKey API is called, AWS KMS generates a unique data encryption key (DEK). The API returns both a plaintext copy of the DEK (for immediate use in client-side encryption) and an encrypted copy of the DEK (wrapped by the customer master key or CMK).
- Usage Pattern: The plaintext DEK is used to encrypt large files or data payloads on the client side, while the encrypted DEK is stored alongside the ciphertext in what is referred to as the “envelope.”
- Security Considerations: Because the plaintext DEK is only temporarily available on the client side, and is never stored or transmitted outside the secure environment, the risk of key exposure is minimized.
- Performance Benefits: By offloading the bulk data encryption to the client, envelope encryption allows AWS KMS to remain focused on key management and API operations, thereby reducing latency and cost.
- Alternative API: AWS KMS also provides a GenerateDataKeyWithoutPlaintext API for scenarios where the plaintext key should never be exposed to the client application immediately. However, for envelope encryption workflows where immediate encryption is required, the GenerateDataKey API is preferred.
The GenerateDataKey API is designed to facilitate efficient and secure encryption for data that exceeds the 4-kilobyte limit imposed by direct KMS encryption.
5.2. Client-Side Encryption Workflow
Once the DEK has been generated, the client-side encryption workflow proceeds as follows:
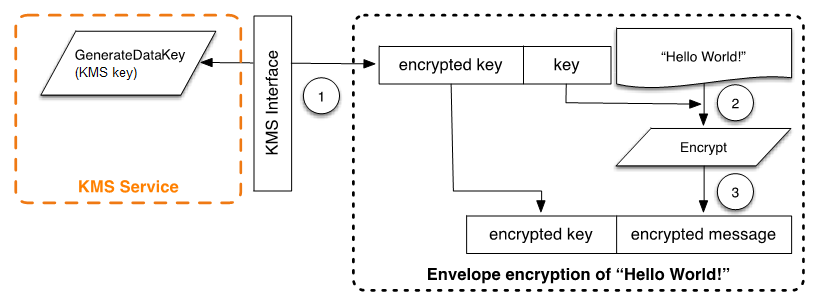
- Encryption of Data: The client application uses the plaintext DEK to encrypt a large file or data stream. This process is carried out entirely on the client side using conventional symmetric encryption algorithms.
- Creation of the Envelope: After encryption, the client creates an “envelope” that includes both the ciphertext (the encrypted data) and the encrypted DEK. The envelope serves as a secure container that bundles the data with the key needed to decrypt it.
- Storage and Transmission: The envelope is stored or transmitted as a single unit. Because the encrypted DEK is part of the envelope, any subsequent decryption operations can reference it.
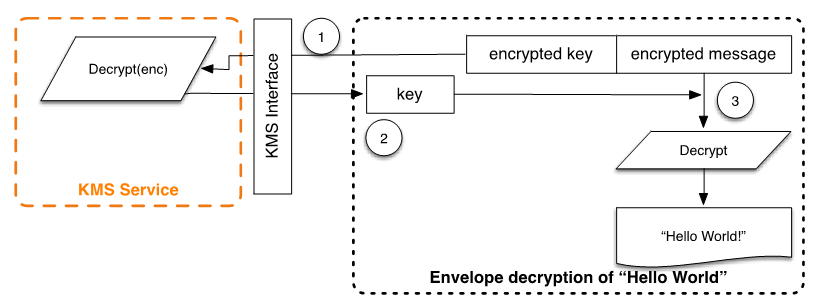
- Decryption Process: When the data needs to be decrypted, the client retrieves the envelope and extracts the encrypted DEK. This encrypted DEK is then sent to AWS KMS via the decrypt API. Once KMS returns the plaintext DEK, the client can use it to decrypt the data locally.
- Cost and Latency Trade-offs: Although envelope encryption requires additional steps, it significantly reduces the number of API calls to AWS KMS, thereby lowering operational costs and reducing latency in high-throughput environments.
- Data Key Caching: To further optimize performance, many implementations—including the AWS Encryption SDK—support data key caching. In such cases, a DEK may be reused for multiple encryption operations within a defined security boundary, reducing the overall frequency of calls to AWS KMS.
Envelope encryption is a powerful technique that balances the security of centralized key management with the performance and scalability of client-side encryption. It is widely used across AWS services and is a critical concept for both architects and security professionals.
6. Key Lifecycle Management
Effective key management extends beyond creation and encryption. It encompasses the entire lifecycle of the key, including rotation, deletion, and recovery. AWS KMS provides a suite of features to help manage keys over their lifespan.
6.1. Key Rotation
Regular rotation of cryptographic keys is a best practice to reduce the risk of compromise. AWS KMS supports both automatic and on-demand key rotation for customer-managed symmetric keys, while AWS-managed keys are rotated automatically.
6.1.1. Automatic and On-Demand Rotation
Automatic key rotation is a feature that allows AWS KMS to rotate the backing key on an annual basis:
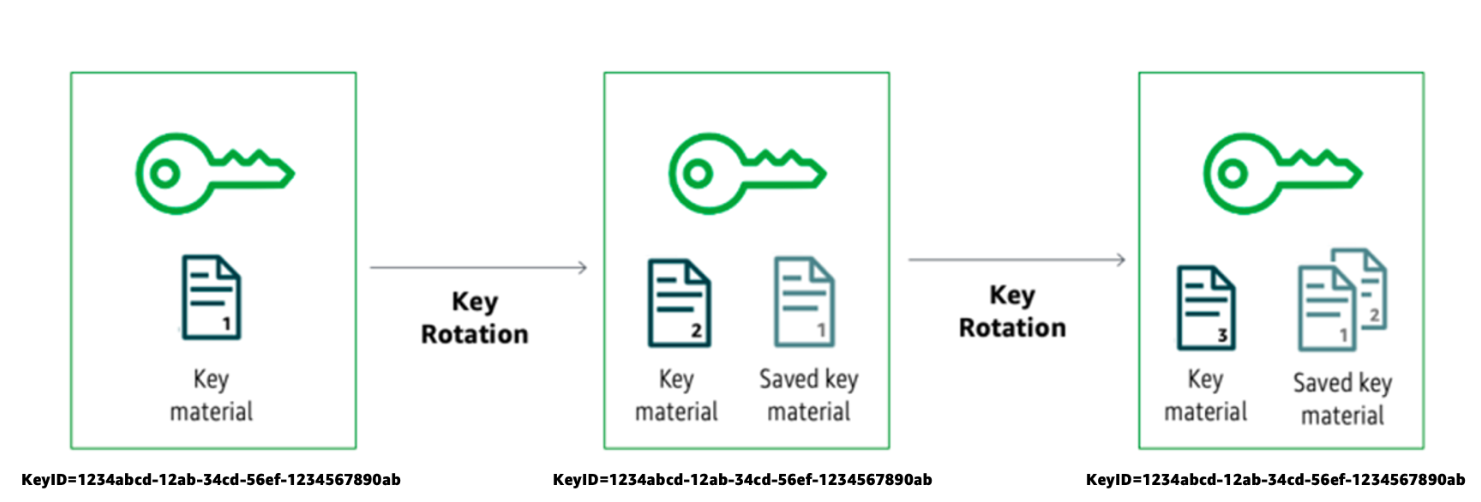
- Annual Rotation: By default, customer-managed symmetric keys can be configured to rotate automatically every 365 days, though the rotation interval can be customized between 90 and 2,560 days.
- Seamless Transition: When a key is rotated automatically, the old backing key remains available for decryption operations. This ensures that data encrypted with a previous version of the key can still be decrypted.
- On-Demand Rotation: In addition to automatic rotation, customers may trigger on-demand rotations. On-demand rotations allow a new backing key to be generated without altering the overall key identifier (the CMK ID), thereby ensuring a seamless transition in client applications.
- Security Considerations: Rotating keys reduces the risk that any single key compromise will lead to extensive data exposure. However, key rotation must be balanced with operational requirements to avoid excessive key reuse that might affect performance.
Automatic and on-demand key rotation are designed to provide a balance between operational simplicity and robust security, ensuring that cryptographic keys remain fresh without interrupting ongoing operations.
6.1.2. Manual Rotation with Aliases
For scenarios where keys are not eligible for automatic rotation—such as asymmetric keys or cases where more frequent rotation is required—manual rotation is the solution:
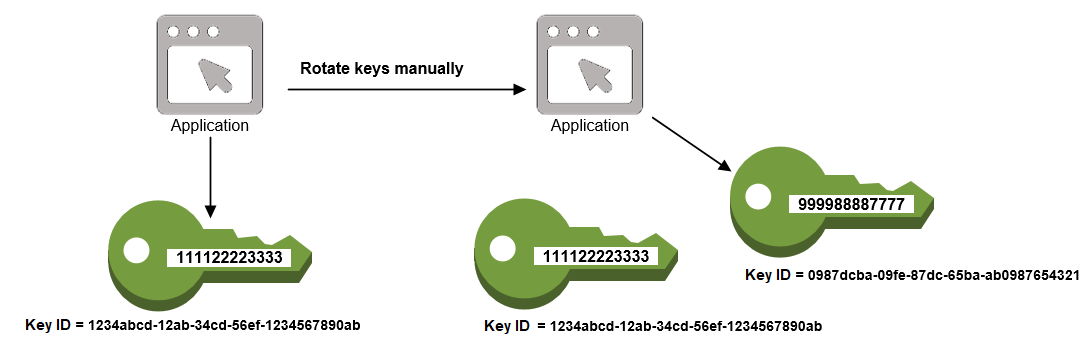
- Creating a New Key: In a manual rotation scenario, a new key is created with a different key ID.
- Using Aliases to Mask Changes: To avoid disrupting applications that reference the key, AWS KMS supports the use of aliases. An alias is a friendly name that points to a specific key ID. When manual rotation is performed, the alias is updated to reference the new key.
- Operational Impact: The previous key remains active to ensure that data encrypted with the old key can still be decrypted. Applications continue to reference the alias, making the rotation transparent to end users.
- When to Use Manual Rotation: Manual rotation is especially useful for asymmetric keys or in situations where regulatory requirements demand more frequent key changes than the standard rotation period.
Manual rotation, while requiring more administrative effort, offers the flexibility to align key rotation schedules with specific operational or compliance requirements.
6.2. Key Deletion and Recovery
The process of decommissioning a key is as important as its creation. AWS KMS provides mechanisms to disable keys, schedule them for deletion, and—in some cases—recover them if deletion was accidental.
6.2.1. Pending Deletion Period
For keys generated within AWS KMS, immediate deletion is not permitted. Instead, the key enters a “pending deletion” state:
- Scheduled Deletion: When a key is marked for deletion, AWS KMS enforces a waiting period of 7 to 30 days. During this time, the key is not available for cryptographic operations.
- Cancellation Option: If a key scheduled for deletion is needed again, the deletion process can be canceled before the waiting period elapses.
- Auditability: Even in the pending deletion state, attempts to use the key are logged via AWS CloudTrail. This logging is essential for compliance and auditing purposes.
- Security Implications: The waiting period provides a safety net against accidental deletion and allows administrators to verify that no critical processes depend on the key.
The pending deletion mechanism is a critical safeguard, ensuring that keys are not removed from the system abruptly, which might otherwise result in irreversible data loss.
6.2.2. Cross-Account Considerations
When dealing with keys that are used across accounts—such as in cross-account sharing of encrypted RDS snapshots—the deletion process requires special attention:
- Coordinated Deletion: For multi-region keys or keys that are used in cross-account scenarios, the primary key cannot be deleted until all replica or dependent keys in other accounts have been deleted.
- Promotion of Replica Keys: In some cases, if a primary key is to be deleted but a replica must remain, the replica can be promoted to become the new primary key before deletion occurs.
- Notification and Monitoring: Integrations with AWS CloudTrail, CloudWatch, and Amazon SNS allow administrators to be alerted if deletion is attempted while the key is in use. Such notifications enable timely intervention to prevent unintended data inaccessibility.
- Operational Workflow: The deletion process in cross-account scenarios is generally more complex, as it may require manual confirmation and careful sequencing of deletion steps across multiple accounts.
Effective key deletion and recovery practices are essential to maintaining operational continuity while ensuring that cryptographic keys are not misused or prematurely destroyed.
7. Security and Access Control
Ensuring that only authorized users and services can access cryptographic keys is a cornerstone of any secure system. AWS KMS integrates with IAM and provides its own native mechanisms—such as key policies and grants—to control access.
7.1. Key Policies
Key policies are JSON-based resource policies that control access to individual KMS keys. They are the primary mechanism for defining which principals (users, roles, accounts) have permissions to perform cryptographic operations on a key.
7.1.1. Default vs. Custom Policies
When a key is created, AWS KMS generates a default key policy that grants full access to the AWS account’s root user. However, customers can modify or replace this default policy with a custom key policy:
- Default Key Policy: The default policy is designed to be simple, giving full control to the root user but relying on IAM for finer-grained permissions. It does not allow access by default unless explicitly granted.
- Custom Key Policy: A custom key policy enables administrators to specify which users or roles have access to specific cryptographic operations, such as encrypt, decrypt, re-encrypt, generate data keys, and more. Custom policies are particularly useful for scenarios involving cross-account access.
- Delegation to IAM: A key policy may delegate authority to IAM policies, allowing users to gain access through their IAM credentials. In this model, the key policy acts as a gatekeeper and establishes the trust boundary for key access.
- Security Best Practices: It is recommended that key policies follow the principle of least privilege, granting only the permissions necessary for each principal to perform their required operations.
The choice between default and custom key policies will depend on the security requirements of the organization and the complexity of the access control model.
7.2. Grants and Temporary Permissions
In addition to key policies, AWS KMS provides a mechanism known as “grants” to delegate temporary permissions:
- Purpose of Grants: Grants allow a key owner to give a specific IAM principal permission to perform certain operations with a key without having to modify the key policy.
- Use Cases: Grants are especially useful for temporary permissions, such as when an AWS service needs to perform a one-time operation on behalf of a user.
- Grant Lifecycle: Grants must be explicitly revoked when no longer needed. They do not expire automatically, so proper lifecycle management is necessary to avoid lingering permissions.
- Implementation: Grants are created via API calls and specify the key ID, the grantee principal, the permitted operations (e.g., encrypt, decrypt, sign, verify), and any additional constraints.
Grants offer flexibility by allowing temporary or one-off access without the overhead of constantly modifying key policies or IAM policies.
7.3. Cross-Account Access Methods
There are several methods to enable cross-account access to a KMS key:
- Key Policy Modification: The key owner can modify the key policy to include principals from other AWS accounts, thereby granting them access to the key.
- IAM Policies in the Target Account: In the account that is receiving access, IAM policies must be configured to allow the necessary KMS operations on the remote key.
- Use of Grants: For scenarios where the external account requires temporary access, grants can be used instead of permanently modifying key policies.
- Assuming IAM Roles: A cross-account access strategy may involve assuming an IAM role in the account that owns the key. This role, once assumed, provides the necessary permissions to perform cryptographic operations.
Cross-account access is critical in multi-tenant environments and when sharing encrypted resources (such as RDS snapshots) across organizational boundaries.
7.4. Authorization Process
The process by which AWS KMS evaluates whether to grant access to a requested operation is complex and involves several layers of checks. The following steps illustrate the typical authorization flow:
7.4.1. SCP, IAM, and Key Policy Evaluation
- Explicit Deny Check: The evaluation begins by checking for any explicit “Deny” statements in the key policy or any related policies (such as Service Control Policies or SCPs). If an explicit deny is found, the request is immediately rejected.
- Service Control Policies (SCPs): If no explicit deny exists, the system next evaluates any SCPs that may restrict access. If the SCP does not allow the action, access is denied.
- VPC Endpoint Policy Check: For private access scenarios using VPC endpoints, the endpoint policy is checked next. If the policy does not permit access, the request is denied.
- Key Policy Evaluation: The key policy is then examined to determine if it explicitly grants the required permissions to the caller. If the key policy grants access, the process moves forward.
- Grant Evaluation: Even if the key policy does not contain an explicit allowance for the caller, the system checks whether any grants are in place that might permit the operation.
- Delegation to IAM Policies: If the key policy delegates access control to IAM, then the IAM policies associated with the caller’s identity are evaluated.
- Cross-Account Considerations: Finally, if the key is being accessed cross-account, additional checks ensure that both the key policy in the owner’s account and the IAM policies in the caller’s account authorize the requested operation.
This multi-step evaluation process ensures that only properly authorized requests are permitted to use KMS keys, providing a robust defense-in-depth mechanism.
7.5. Condition Keys (kms:ViaService, kms:CallerAccount)
AWS KMS also supports special condition keys that can be used within key policies to further restrict access:
- kms:ViaService: This condition key allows administrators to specify that a key can only be used by particular AWS services. For example, a key might be restricted so that only Amazon EC2 or RDS can use it. This helps enforce service-specific encryption policies.
- kms:CallerAccount: This condition key restricts key usage to principals from a specific AWS account. It is particularly useful in cross-account scenarios to ensure that only identities from a trusted account can perform operations on a key.
The use of these condition keys provides an additional layer of security by allowing precise control over how and where a key can be used.
8. Asymmetric Encryption and Signing
While symmetric keys dominate many encryption scenarios in AWS KMS, asymmetric keys provide capabilities that are indispensable for secure key exchange, digital signatures, and public key infrastructure (PKI).
8.1. Key Pairs and Use Cases
Asymmetric encryption involves the use of key pairs, consisting of a public key and a private key:
- Public Key: The public key is used for encryption or verifying digital signatures. Since it can be shared openly, it is often distributed to external parties or embedded in applications.
- Private Key: The private key is used for decryption or for signing data. This key is highly sensitive and is never exposed in plaintext outside of AWS KMS.
- Use Cases: Asymmetric keys are used for encrypting data where the encryption operation may be performed outside of AWS, for digital signing to ensure data integrity, and for scenarios where secure key exchange is required.
- Supported Algorithms: AWS KMS supports multiple asymmetric algorithms, including RSA for both encryption/decryption and signing/verification, Elliptic Curve Cryptography (ECC) for signing and verification, and—for regions in China—SM2 keys.
- Security Model: The private key, even though it is used for decryption or signing, never leaves the secure boundary of AWS KMS in an unencrypted form. All operations that require the private key are performed within AWS KMS via API calls.
Asymmetric keys extend the flexibility of AWS KMS by enabling secure interactions with external systems and applications that require public key cryptography.
8.2. Digital Signing Workflow
Digital signing is a cryptographic technique used to verify the authenticity and integrity of data:
- Creating a Digest: To digitally sign a large file or document, the client first computes a digest (a cryptographic hash) of the data. The digest is a fixed-size string that uniquely represents the file’s contents.
- Signing the Digest: The client then uses AWS KMS to sign the digest. During this process, the private key held by AWS KMS is used to create a digital signature. The digital signature is a cryptographically secure token that can later be used to verify that the file has not been altered.
- Distributing the Signed Data: The file, along with its digital signature, is transmitted to the recipient. The recipient uses the public key (which is available for download) to verify the signature.
- Verification Process: The recipient computes the digest of the received file and uses AWS KMS’s verify API to compare the computed digest with the signature. If they match, the integrity and authenticity of the file are confirmed.
- Applications: Digital signing is used in document e-signing, secure messaging, authentication tokens, and many other scenarios where data integrity is of paramount importance.
By providing robust support for digital signing and verification, AWS KMS plays a vital role in securing communications and ensuring that data has not been tampered with during transit.
9. Performance and Optimization
Given the critical role that AWS KMS plays in securing data, it is important to understand the performance characteristics of the service and the optimization strategies that can be employed to balance security, cost, and latency.
9.1. API Limits and Throttling
AWS KMS enforces service limits to ensure the stability and performance of the system:
- Request Limits: There are limits on the number of API requests that can be made to AWS KMS per second. Exceeding these limits can result in throttling, which may impact application performance.
- Cost Implications: Each call to AWS KMS is billed. Frequent calls—especially in high-throughput applications—can result in significant costs.
- Mitigation Strategies: To mitigate the risk of throttling, applications should consider strategies such as batching encryption operations, optimizing the frequency of key generation calls, and employing client-side caching techniques.
- Monitoring: AWS CloudWatch and CloudTrail provide detailed metrics and logs related to KMS usage. These tools can be used to monitor API usage, detect throttling events, and optimize application performance.
Understanding and managing API limits is essential for maintaining both performance and cost efficiency in environments that rely heavily on AWS KMS.
9.2. Data Key Caching Strategies
Data key caching is a powerful technique used to reduce the number of API calls to AWS KMS:
- Reuse of Data Keys: Instead of generating a new data key for every encryption operation, data key caching allows the reuse of a data key for a configurable period, number of bytes, or number of messages.
- Performance Benefits: By caching data keys, applications can significantly reduce latency and the cost associated with frequent calls to the GenerateDataKey API.
- Security Trade-Offs: While reusing data keys can improve performance, it does introduce some security trade-offs. Reusing a key over a longer period or for encrypting larger volumes of data increases the risk that the key may be compromised.
- Implementation: The AWS Encryption SDK, among other libraries, supports data key caching via a local cryptographic materials cache. This cache can be configured with policies that specify the maximum age, the maximum bytes encrypted, or the maximum number of encryption operations before a new data key is fetched.
- Balancing Act: The decision to cache data keys should be made based on the specific security and performance requirements of the application. The goal is to find an optimal balance where the benefits of reduced API calls do not compromise the overall security of the data.
Data key caching is one of the most effective ways to optimize encryption performance in a high-throughput environment while still maintaining strong security controls.
10. Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) is a method for managing access to resources based on attributes (or tags) rather than fixed identities:
- Concept Overview: With ABAC, permissions to use a KMS key can be granted based on resource tags. For example, a key tagged with “environment:prod” can be accessed only by users whose IAM policies specify that they can work with production keys.
- Scalability: ABAC simplifies access management at scale. Instead of defining detailed policies for each individual key or user, organizations can rely on tag-based policies to grant or restrict access.
- Implementation in KMS: In AWS KMS, ABAC is implemented by allowing key policies to include conditions that check for specific tag values on the KMS keys. Similarly, IAM policies can be written to reference these tags, ensuring that only authorized users can perform cryptographic operations on keys with matching attributes.
- Benefits: ABAC enhances security by reducing the administrative overhead of maintaining explicit user or role-based permissions. It also makes it easier to adapt to changes, such as when keys are reclassified or moved between environments.
- Security Considerations: As with any access control mechanism, careful design and testing of ABAC policies are critical. The policies must be precise and follow the principle of least privilege to ensure that only the intended users are granted access.
ABAC is a modern, flexible approach to access control that can greatly simplify the management of cryptographic keys in complex, dynamic environments.
11. Conclusion
In summary, AWS KMS is more than just a key management service—it is a comprehensive platform that supports a wide range of encryption scenarios and security requirements. Whether you are encrypting sensitive data at rest in S3, protecting EBS volumes, securing RDS databases, or ensuring the integrity of cross-region applications, AWS KMS provides the necessary tools and capabilities to safeguard your data in the cloud.